Sophos recently released its annual report the (Sophos The State of Ransomware 2023) where in it mentioned that in spite of persistent Data encryption there has been tremendous rise in Ransomware attacks affecting nearly 75% organizations and their revenue. Due to rising incident cost it affected the revenue as ransom was paid.
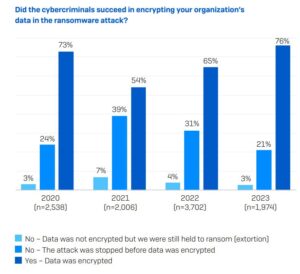
Data encryption has continued to rise, with adversaries succeeding in encrypting data in over three quarters (76%) of ransomware attacks. In fact, encryption levels are now at their highest point in the last four years. This likely increase reflects the ever-increasing skill level of adversaries who continue to innovate and refine their approaches.
Root cause of Ransomware:
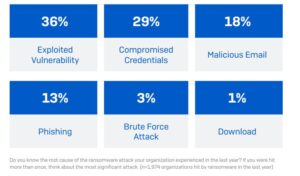
The root cause for ransomware per the Sophos report the most common was an exploited vulnerability (involved in 36% of cases), followed by compromised credentials (involved in 29% of cases).
Further organizations paid ransom to get data decrypted that doubled their recovery cost as mentioned and put pressure on revenue ($750,000 in recovery costs versus $375,000 for organizations that used backups to get data back).
Usually when organization pat ransom, the recovery to encrypted data takes long time so organisations who always use backups recover within a week and survey say 45% used back up compared to 39% who didn’t use back up and paid ransom.
Moreover, paying the ransom usually meant longer recovery times, with 45% of those organizations that used backups recovering within a week, compared to 39% of those that paid the ransom.
These findings align almost exactly with Sophos’ latest retrospective analysis of 152 attacks that our Incident Response and Managed Detection and Response (MDR) teams were brought in to remediate, where 37% started with an exploited vulnerability and 30% with compromised credentials.
Emails were the root cause of 30% (with rounding) of attacks: 18% started with a malicious email and 13% with phishing. 3% began with a brute force attack and just 1% with a download.
Fig 1
Root Cause of Ransomware attack by adversaries:
Key findings from Sophos report include:
In 30% of cases where data was encrypted, data was also stolen, suggesting this “double dip” method (data encryption and data exfiltration) is becoming commonplace.
The education sector reported the highest level of ransomware attacks, with 79% of higher education organizations surveyed and 80% of lower education organizations surveyed reporting that they were victims of ransomware.
Overall, 46% of organizations surveyed said they used data back up before data encryption before they paid ransom. However, larger organizations were far more likely to pay. In fact, more than half of businesses with revenue of $500 million or more paid the ransom, with the highest rate reported by those with revenue over $5 billion. This could partially be due to the fact that larger companies are more likely to have a standalone cyber insurance policy that covers ransom payments.
“Experienced analysts can recognize the patterns of an active intrusion in minutes and spring into action. This is likely the difference between the third who stay safe and the two thirds who do not. Organizations must be on alert 24×7 to mount an effective defense these days,” said Wisniewski.
Rate of Data Encryption
Data encryption has continued to rise, with adversaries succeeding in encrypting data in over three quarters (76%) of ransomware attacks. In fact, encryption levels are now at their highest point in the last four years. This likely reflects the ever-increasing skill level of adversaries who continue to innovate and refine their approaches.
Success rate of data encryption by cyber criminals by year
Fig 2
Data Recovery
97% of organizations that had data encrypted got data back. Backups were the most common approach, used in 70% of incidents. 46% paid the ransom and got data back, while 2% used other means. Overall, one in five (21%) used multiple methods to restore their data. 1% of organizations that had data encrypted paid the ransom but didn’t get data back.
Data Recovery by Country
Respondent in Sophos report in E MEA reported higher aggregate levels of backup use (75%) and lower aggregate levels of ransom payments (40%) than those in the Americas (65%/55%) and Asia Pacific (67%/49%).
At a country level, France has the highest level of backup use (87%), closely followed by Switzerland (84%).
The importance of backups is demonstrated when we see that the two countries least able to use backups to restore data, Italy (55%) and Singapore (57%), are also the two countries that reported the lowest overall data recovery rates (93% and 90%, respectively).
Italy also reported the highest propensity to pay the ransom (56%), closely followed by the U.S. and Brazil (both 55%). In most cases, organizations that paid the ransom were able to recover data. However, in France and the UK, around one in ten organizations that paid the ransom did not get any data back.
The Impact of Cyber Insurance on Data Recovery
Cyber insurance forms a crucial element that considerably will help recover encrypted data then those without policies.
The report from Sophos stated 98% of those with a standalone policy and 97% of those with a wider insurance policy that covers cyber insurance, got data back. In comparison, 84% of those without a policy were not able to get encrypted data back.
“Sophos’ latest report is a clarion reminder that ransomware remains a major threat, both in scope and scale. This is particularly true for ‘target-rich, resource-poor’ organizations that don’t necessarily have their own in-house resources for ransomware prevention, response and recovery,” said Megan Stifel, executive director of the Ransomware Task Force and chief strategy officer, Institute for Security and Technology. “One way to boost security, which is aligned with Sophos’ findings in the report, is to implement the Ransomware Task Force’s Blueprint for Ransomware Defense, a framework of 48 safeguards based on the CIS IG1 Controls.
(Image courtesy: www.abijita.com)
