Today, a marked shift is evident from a conventional cybersecurity approach based on “trust but verify” to a “zero trust” model. In continuation of our series “Unraveling Security”, IBM and SMEVenture organized the second webinar on “Zero Trust to Protect Internal & External Users.” The webinar focused on how Zero Trust Model can help organizations reduce the risks of advanced persistent threats across their systems and eliminate compromised credentials, especially in a remote work scenario.

Zero Trust to Protect Internal & External Users I Unravelling Security
The second session “Zero Trust to Protect Internal & External Users” was organized on 24th-Feb-2022 and led by Mr. Tushar Haralkar, Country Technical Leader, IBM Security for India-South Asia. The session focused on the role of the identity of organizations’ general and privileged users and its significance in the zero trust journeys.
Why Do Organizations Need Zero Trust?
The digital transformation during the past decade has marked a shift in the way businesses operate. Digital adoption has rapidly picked up the pace, especially during the past two years. Exponentially growing and distributed data across the network, cloud adoption, and remote work culture have made the need for cybersecurity stronger than it ever was. Following factors contribute to the risk of cyberattacks:
- User & Endpoints: The enhanced access to data from anyone using any device situated anywhere.
- Increased Data Distribution: Apart from networks, data has now become a shared resource for users and applications, reducing the visibility and paving the way for cyber attacks with the least detection.
What are the Basic Elements of Zero Trust?
The three key elements that constitute zero trust strategy are:
- To never trust and always verify
- Allowing minimal privileges
- Assume intent to breach
Mr. Tushar Haralkar said, “The Zero Trust journey focuses on allowing the right user to have the access to the right data at the right time.” The aim is to allow limited channels for any data breach. Then, Mr. Tushar Haralkar went on elaborating how MFA possesses various cybersecurity gaps and how zero trust is viable to be used in different aspects due to its scalability and high speed.
Why is Multi-Factor Authentication not the Holy Grail against Cyberattacks?
While industry giants use Multi-factor authentication to prevent compromised credentials, the framework itself is prone to device spoofing by text messages, malware attacks, email phishing, session hijacking, SIM swaps, etc. Second, studies show that around 40% of consumers leave online purchases and transactions halfway because of the complexities of two-factor authentication significantly reducing sales and successful logins into applications.
How IBM’s Security Verify is a Promising Solution?
IBM’s Security Verify is a comprehensive, AI-ML-driven digital identification engine built with zero trust security in mind. In order to provide a frictionless yet secure user experience, this solution extends beyond MFA to detect identity-related risks such as malware and unsafe Wi-Fi usage.
The Security Verify model analyzes the user activity based on various factors to generate a risk score that organizations across various sectors can use to reduce security attacks considerably.
What Are the Use Cases of IBM’s Security Verify Solution?
- Fraud Detection during login using behavioral biometric layered authentication using user’s typing speed, copy-pasting of user credentials
- Two-factor authentication and dynamic linking
- Bot detection that allows the bot to login but deny the transactions
- Phishing identification by detecting phishing sites and compromised credentials usage
Analyzing the user’s activity based on various parameters, the Security Verify lets the organization decide the next step based on the risk score. The risk score considers spoofing, infection, time zones, login frequency, Omnichannel consistency, velocity platform, matched screen DPi, etc. Mr. Tushar then presented a live demonstration of how Security Verify can detect various anomalies and warn the organization about the risk insights associated with user login and activity.
Relevant reads: https://smeventure.com/cybersecurity-the-need-of-the-21st-century/
Zero Trust and Its Use Cases
1. Ensuring Data Privacy Conforming to Policy Guidelines
2. Protecting the Hybrid Cloud
3. Decrease the Insider Data Breach Risks
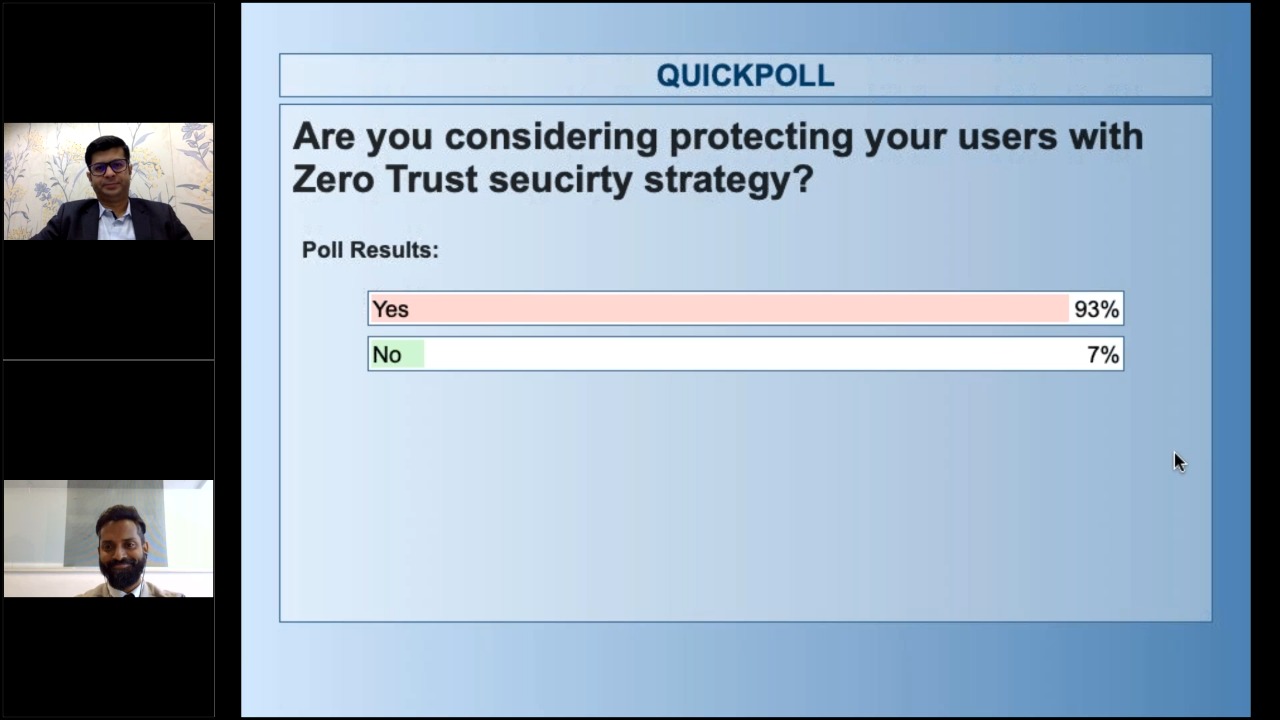
To make the session more captivating and understand audience’s concerns with relation to cyber attacks and security, we also organized two polls.
- What are your biggest concerns around protecting your users inside and outside your organization?
 2. Are you considering protecting your users with a Zero Trust security strategy?
2. Are you considering protecting your users with a Zero Trust security strategy?
At the end of the webinar, Mr. Tushar Haralkar answered the audience’s questions about the workshop and the cyber kill cycle.
Zero Trust Security Strategy revolutionizes how enterprises view and respond to cyber security threats. As malware and phishing attacks become ever more common, new vulnerabilities can be found in abundance inside the organization, contrary to what the industry previously believed about the inner zone of network perimeters being attack-proof. Advanced persistent threats (ATPs) are on the rise, and organizations’ perimeter security must be redesigned to meet the attackers’ approach.
Watch Unravelling Security Series Part 1 Webinar: https://www.youtube.com/watch?v=kIqc8jjfgqU
Written by,
Prasad P. Patkar
